How to Use AI for Cybersecurity
The traditional Security Operations Center is becoming a relic of cybersecurity's past. While legacy SOC architectures struggle with unreasonably high MTTD and analysts drowning in 10,000+ daily alerts, a fundamental shift is reshaping how we think about security operations. The future isn't about bigger SIEM dashboards or more analysts. It's about autonomous AI SOC agents that transform SOC architecture from reactive command centers into proactive, intelligent defense ecosystems.
The SIEM-Centric Bottleneck That's Killing SOCs
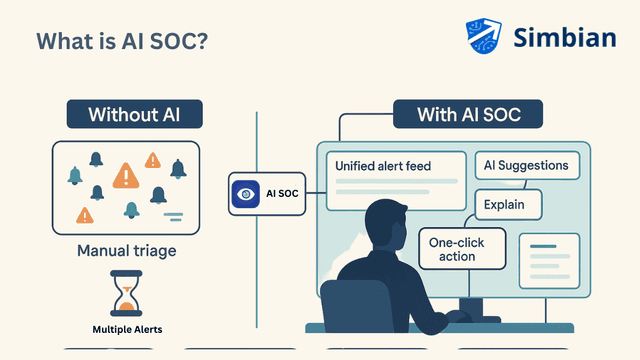
For decades, SOC architecture has revolved around a flawed but straightforward premise: funnel everything through the SIEM. Every log, every alert, every threat indicator gets processed through centralized security information and event management systems before human analysts can take action. This forces cybersecurity analysts to constantly switch between tools, manually correlate data, and burn out from information overload.
Traditional SOC design assumes humans can orchestrate dozens of security tools into a coherent defense. But when AI cyberattacks operate at machine speed and defenders think at human pace, the gap becomes insurmountable.
The AI SOC Revolution
Modern SOC architecture flips the traditional model entirely. Instead of centralizing everything through SIEM bottlenecks, AI SOC deploys autonomous AI SOC agents directly at data sources, endpoints, networks, cloud platforms, and identity systems. These agents don't wait for human commands; they investigate, correlate, and respond autonomously while keeping analysts informed.
Autonomous SOC Changes Everything:
Context-Aware Decision Making: Unlike rule-based automation, AI agents understand business context and organizational priorities
Distributed Intelligence: Agents operate where data lives, eliminating centralized bottlenecks. No playbooks required!
Continuous Learning: Every investigation improves future threat detection and response
Traditional SOCs need conductors (analysts) to coordinate every instrument (security tool). AI-native SOCs enable expert musicians (autonomous AI SOC agents) to improvise together, creating better outcomes with less overhead.
The Three Pillars of Autonomous SOC Architecture
1. Context Lake™: Simbian's Context Lake technology represents the foundational shift from siloed security data to unified organizational intelligence. Unlike traditional data lakes that store raw logs, Context Lake maintains living knowledge about business relationships, asset criticality, user behavior patterns, and threat context.
This means AI agents don't just detect anomalies—they understand whether that suspicious login represents a genuine threat or a remote employee accessing systems from vacation. Context makes the difference between noise and intelligence.
2. TrustedLLM™: Generic AI assistants weren't built for life-or-death security decisions. TrustedLLM eliminates the hallucination problems that plague consumer AI by grounding responses in verified security intelligence and organizational data.
3. Multi-Agent Orchestration: Modern attacks span multiple domains—email, endpoints, networks, cloud platforms, and identity systems. Single-point solutions miss the connections. Multi-agent architectures deploy specialized AI agents across every attack surface, coordinating investigations and responses in real-time.
Instead of human analysts manually correlating events across disparate tools, AI agents share intelligence instantaneously, building complete attack timelines and responding holistically to threats.
AI-native SOC architecture doesn't replace security professionals—it liberates them. When autonomous agents handle routine investigation, correlation, and initial response, analysts can focus on strategic security initiatives.
The goal isn't to replace humans with AI; it's to have more effective analysts who can think strategically instead of drowning in operational tasks.
Overcoming Traditional SOC Problems
To overcome traditional SOC problems marred by slow and uncontrolled SOARs, we propose an implementation plan:
Phase 1: Agent-Assisted Investigation - Deploy AI SOC agents to accelerate manual investigation workflows, proving value while building confidence in autonomous capabilities.
Phase 2: Automated Response - Enable agents to take autonomous action on well-understood threats—malware isolation, phishing email quarantine, suspicious user account lockdown.
Phase 3: Predictive Defense - Leverage Context Lake intelligence for proactive threat hunting and risk assessment that prevents attacks before they succeed.
Phase 4: Autonomous Operations - Achieve 24/7 autonomous threat detection and response with human oversight focused on strategic security decisions.
AI for Cybersecurity
SOC architecture is experiencing its most fundamental transformation since the invention of the SIEM. Organizations can either cling to centralized, human-dependent models that can't scale with modern threats, or embrace AI-native architectures that deliver autonomous intelligence at machine speed.
The choice isn't between human analysts and AI agents—it's between empowered analysts supported by intelligent automation and overwhelmed analysts drowning in manual processes.
Experience the future of SOC architecture. Discover how Simbian's autonomous AI agents transform security operations through Context Lake intelligence, TrustedLLM reasoning, and 24/7 autonomous threat detection that never sleeps, never burns out, and never misses critical threats.