Complete SecOps Automation with Superintelligent AI Agents
Four autonomous agents in one unified platform. One Context Lake powers every decision. When one agent learns, they all adapt—the security platform that solves problems instead of just flagging them.
Trusted by leading enterprises and MSSPs
Architect AI-Powered SecOps
Best AI for Cybersecurity
AI NetSecOps Agent
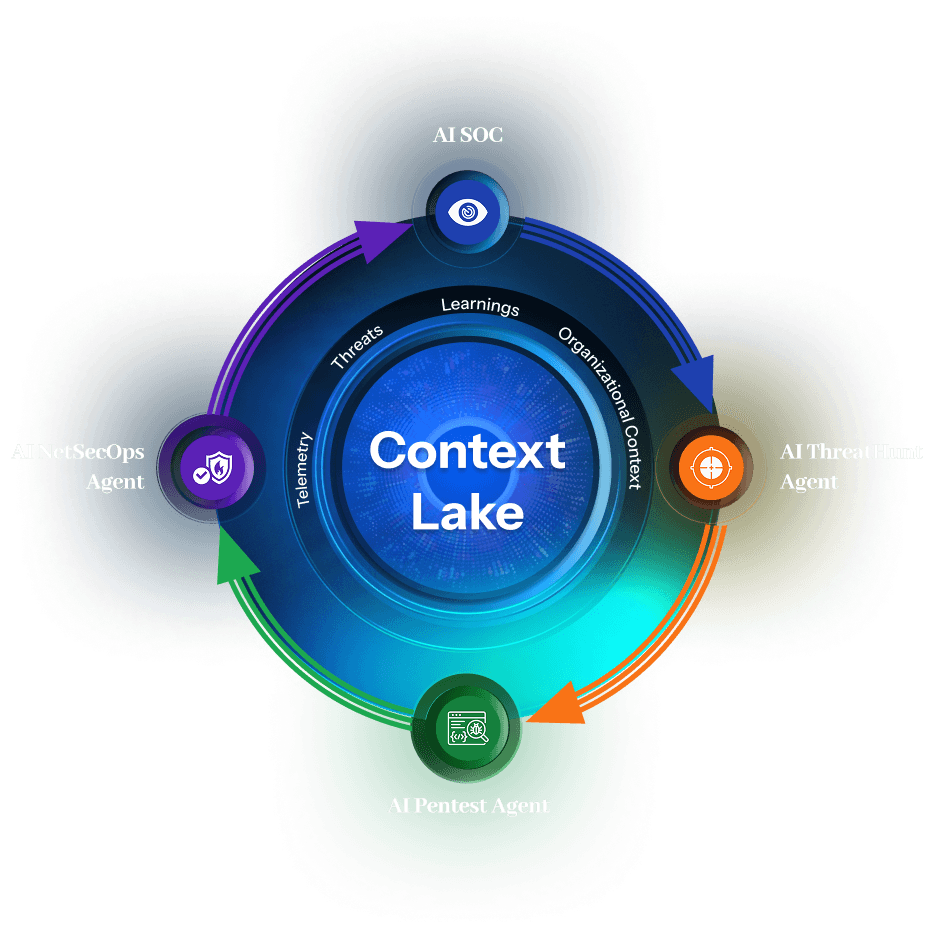
Context Lake:
The Intelligent Backbone of Autonomous Security
Unlike siloed tools, every Simbian agent has access to a unified intelligence layer. It captures tribal knowledge, telemetry, organizational context, threat intelligence, and learnings from every investigation.
When your SOC Agent detects an anomaly, Context Lake learns about it. Your Threat Hunt Agent immediately sees the pattern. Your Pentest Agent flags related vulnerabilities. Your Network Security Agent proactively blocks similar behavior.
Best AI for Cybersecurity
Introducing the first benchmark to comprehensively measure LLM performance in Security Operations Center (SOC).
One platform.
Four Agents.
Limitless Defense.
Each agent masters its domain. Together, they eliminate risks.
AI SOC Agent
Simbian's AI SOC Agent autonomously triages, investigates, and responds to alerts 24x7x365 from your SIEMS, XDRs, and other sources of alerts by combining the best of Simbian's security knowledge base, and your organizational knowledge.
AI Threat Hunt Agent
Simbian's AI-Powered Threat Hunt Agent accelerates detection of stealthy threats by leveraging your existing telemetry. Amplify your threat hunting productivity by 5-10x.
AI Pentest Agent
Simbian's AI Pentest Agent transforms expensive, point-in-time compliance checks into a continuous, on-demand security practice. It leverages your unique context to first identify and then help resolve vulnerabilities more efficiently within your SecOps workflow.
AI NetSecOps Agent
Simbian's AI NetSecOps Agent autonomously manages firewall policies, prevents outages, and responds to threats 24/7. It handles the full operational lifecycle, eliminating manual toil and returning 80% of your team's time.

Context Lake Fuels Decisions,
Simbian Agents Make Them Smart
Simbian Context Lake™
Simbian Context Lake™
Harness the power of organisational context and tribal knowledge for every action the agent takes. Notes, verdicts, and exceptions persist, so every workflow starts with fewer wrong assumptions.

SOC Sparks Hunting
SOC Sparks Hunting
Confirmed incidents create hypotheses, so hunting begins with what likely went wrong elsewhere.

Hunting Reuses Triage
Hunting Reuses Triage
Hunt results get validated like alerts—rapidly separating real threats from benign noise.

Pentest Prioritizes Changes
Pentest Prioritizes Changes
Exploitable vulnerabilities steer hunts and testing toward the attacker's most realistic routes.

NetSecOps Executes Changes
NetSecOps Executes Changes
Turn findings into safe policy updates, IOC blocks, and containment—then document outcomes automatically.
Why Simbian?
Simbian's AI Security Agents empower, not replace, your security analysts, automating alert triage, threat hunts, and penetration tests, so your team can focus on what matters most, 24/7.
Simbian powers some of the world's largest SOC teams. Simbian Agents are deployed in days and demonstrate ROI within the first week.
Simbian's AI Agents work together across SOC, threat hunt, and pentest to provide unified, modern SecOps that gets smarter every time you use it.
Simbian captures your unique security context, building on the knowledge of your team, then uses that context to generate precision response and build a living playbook.





