Loading...
Loading...

We have great news for all threat hunters today! We are pleased to announce our joint work with Microsoft to make threat hunting faster, broader, deeper for Microsoft 365 E5 customers.
Let’s say you receive a tip that someone is targeting your billing team, possibly to access your customer database. You are concerned that you don’t have sufficient detections to catch this. So you begin a threat hunt. Your mission is clear—find if the threat actor has reached your users or assets, where, when, how.
Threat hunts invariably start with incomplete information about the threat actor and their techniques. You use your intuition to formulate hypotheses about how and where the threat actor is operating. Then you “execute” the hunt i.e. gather relevant data from your security tools, analyze it, chase the leads. Then you refine your hypothesis and repeat till you find the threat actor. This exercise can take multiple days of your best people, with no guarantee of results.
That “execute” phase is the most arduous.
You must be fast. You must be smart about which leads you pursue. You are in a race with a moving target.
You must hunt discreetly. Asking other employees for information may tip off the threat actor if they happen to be an insider.
You must search through a large space. The threat actor activity you are looking for could have occurred over many months.
You may need to search through diverse logs from tools you are not familiar with. The evidence you need may be scattered across the enterprise.
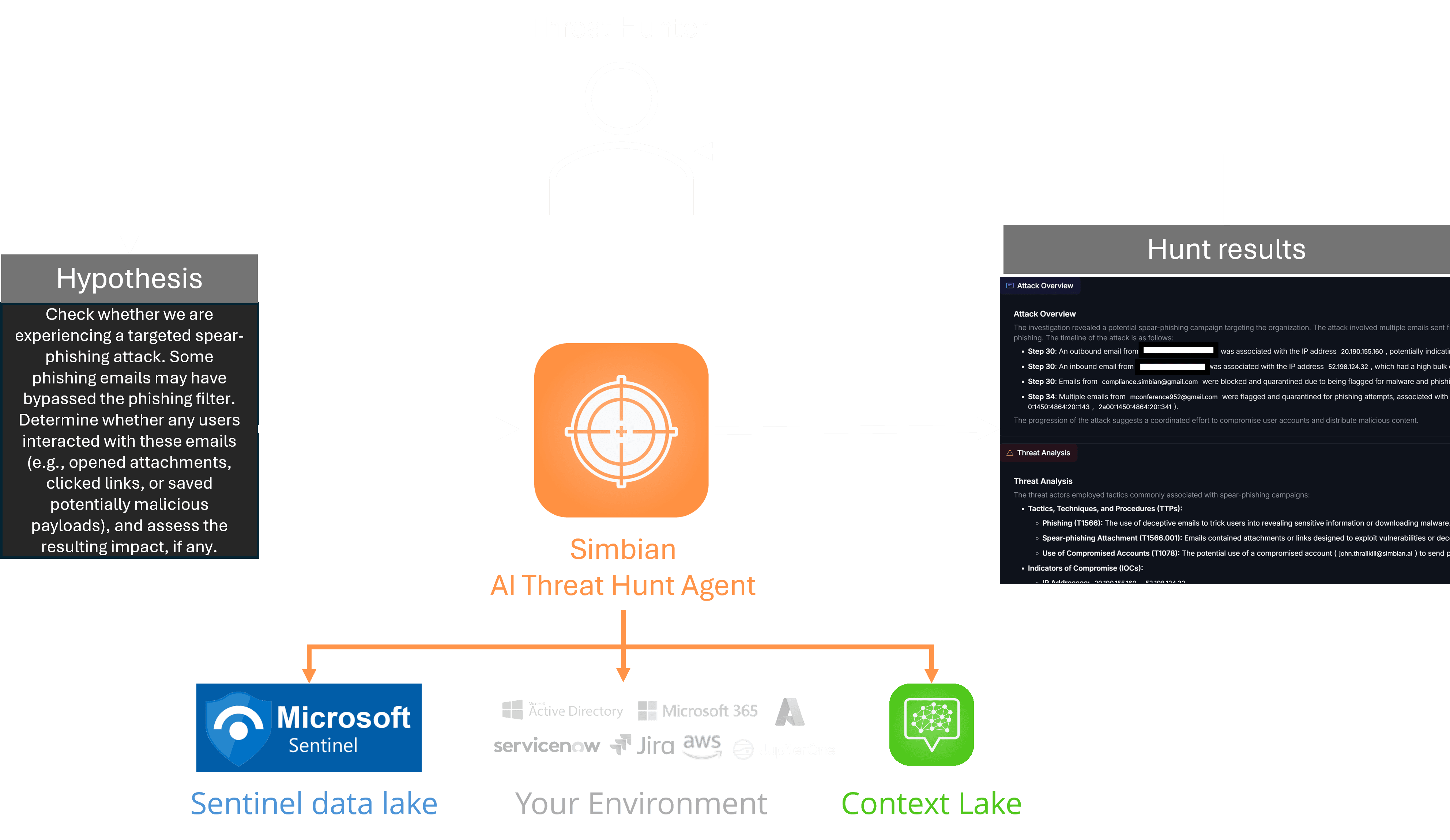
Simbian’s AI Threat Hunt Agent, announced in private preview today, scales threat hunting by offloading the execute phase of the threat hunt.
You provide the Agent your hunt hypothesis in natural language. It maps your hypothesis to TTPs using AI and gathers relevant data from your organization’s tools using its rich ecosystem of integrations. It analyzes the data and chases promising leads, pivoting as needed, to find evidence supporting your hypothesis. Based on the results or lack thereof, you then refine the hypothesis and iterate.
You save time by offloading the laborious part of threat hunting.
You can cast your net wide and validate multiple hypotheses in parallel using the Agent, potentially concluding the hunt more quickly.
You are able to hunt more discreetly. The Agent gathers and analyzes data on your behalf, using organizational context it has gathered over time. This reduces the number of times you need to reach out to other employees to understand the context for the activity you are observing.
The threat actor activity you are looking for could have occurred over many months, and may be scattered across the enterprise. This is where Microsoft’s Sentinel data lake comes in—it extends the Microsoft Sentinel platform with a cloud-native security data lake that allows you to ingest, store, and analyze large volumes of diverse security data at scale, in a single, open-format, extensible platform.
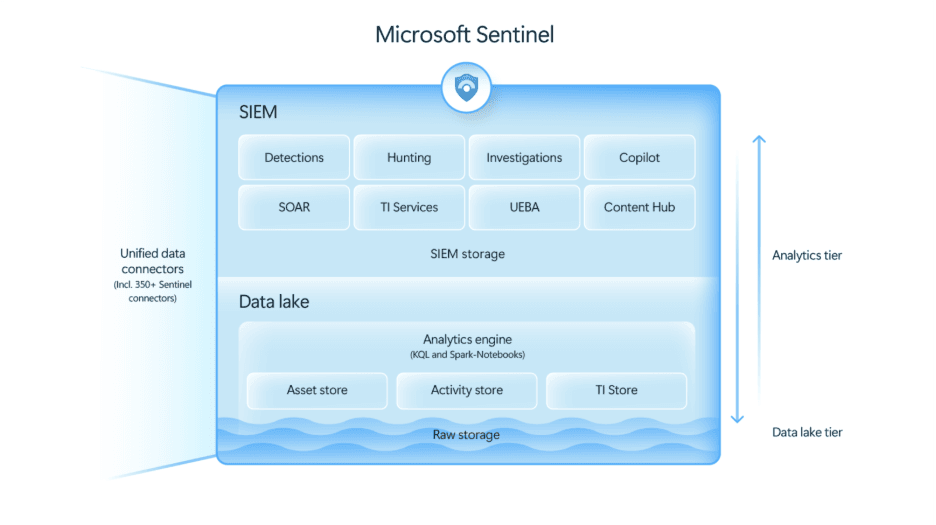
As a Microsoft 365 E5 customer, you can bring all your security data into the Sentinel data lake cost-effectively, removing the need to choose between coverage and cost. Simbian’s AI Threat Hunt Agent uses your Sentinel data lake to reason across months of diverse logs from throughout the enterprise.
Simbian is honored to be in Microsoft’s preview program for Sentinel data lake, to address our mutual customers’ pain point in threat hunting. Sentinel data lake is now Generally Available.
Let’s take the scenario that this post started with—someone is targeting your billing team, perhaps to get to your customer database. Let’s say your starting hypothesis as a threat hunter is that your billing team is getting spearfished. You start a new threat hunt in Simbian’s AI Threat Hunt Agent and enter this hypothesis.
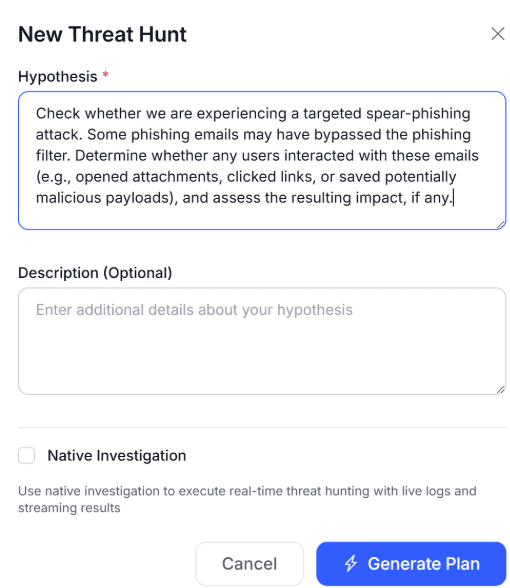
Prior to this step, during deployment the Simbian platform was granted access to the organization’s Sentinel data lake as well as other data sources needed for investigation. Simbian has integrations with over 75 security and enterprise tools including all major SIEMs, EDRs, Email Security solutions.
In the first phase the AI Threat Hunt Agent maps the user-provided hypothesis to known techniques. It figures out from the data sources connected to the Simbian platform which tables have data relevant to those techniques. It then creates a sequence of queries to find activity that potentially matches the hypothesis. This phase is a broad sweep that may yield some false positives, as benign activity in the organization can sometimes match the pattern of bad actors.
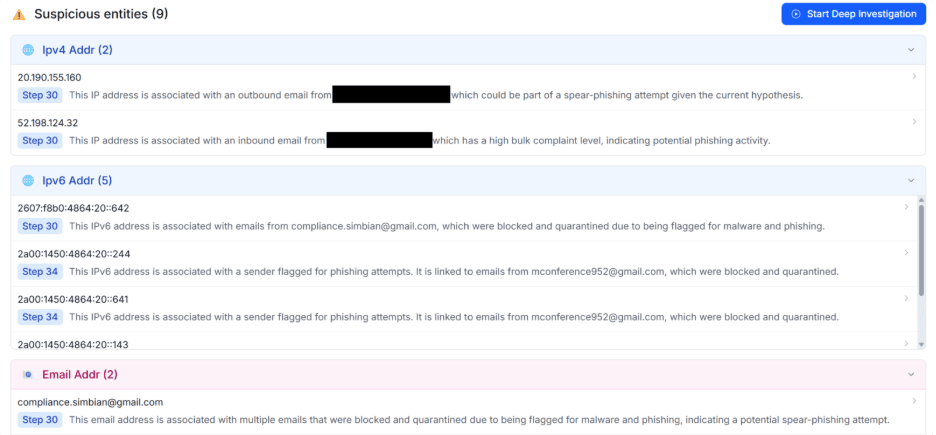
The AI Threat Hunt Agent investigates these candidates deeply to separate the true and false positives. It recommends sub-groups of results from the first phase to investigate further as one unit, because they are linked to a common hunting rationale. These sub-groups and the supporting rationale are conceptually analogous to alerts from a detection engine. This allows the threat hunter to optionally optimize the AI Threat Hunt Agent’s investigation.
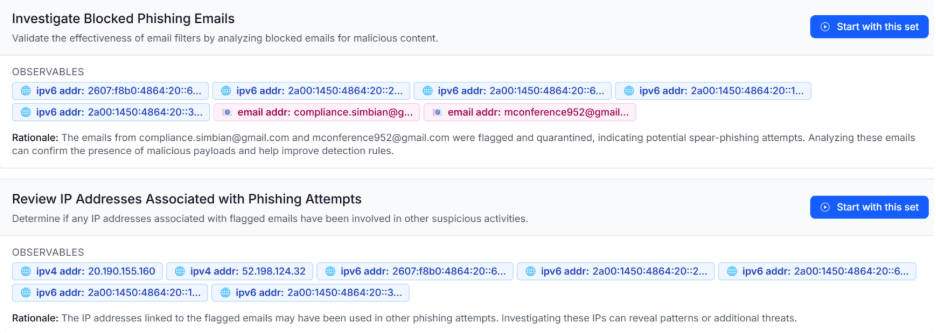
The AI Threat Hunt Agent then looks for sufficient evidence of malicious activity around those candidates to have high confidence that it is a true positive. It uses data from all tools across the organization that it has been given access to, as well as organizational context gathered over time in Simbian’s Context Lake.
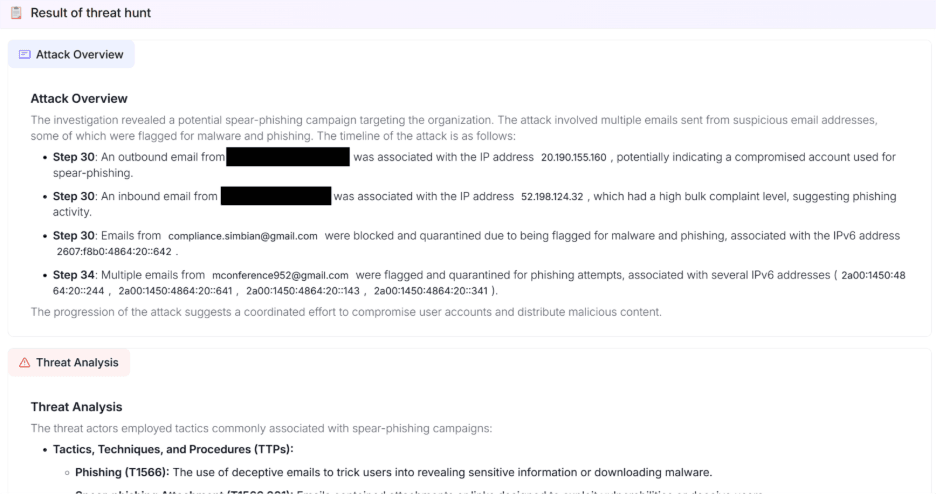
Once the deep investigation concludes, the AI Threat Hunt Agent compiles the results of what was found.
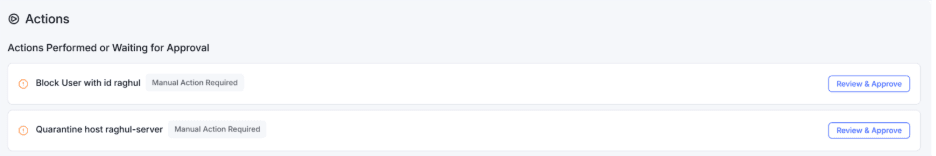
As the AI Threat Hunt Agent finds and investigates suspicious activity, it also automates containment actions. You can review and approve each action, or you can configure the Agent to auto-execute these actions to shut down attacks fast.
Simbian's new AI Threat Hunt Agent in coordination with the previously released Simbian AI SOC Agent completes the lifecycle of threat hunting. Threat hunters formulate hypotheses informed by security context gathered in their Simbian Context Lake™, then validate those hypotheses with Simbian’s AI Threat Hunt Agent. Simbian's AI SOC Agent is used to investigate and respond to threat hunt findings.
Threat hunting is one of the hardest roles in security. We are excited to share our progress here to make threat hunting fast, broad, deep, and hopefully fun. With the efficiencies gained we hope organizations will scale out their threat hunting and shift left to hunt more proactively. Simbian’s AI Threat Hunt Agent is in private preview. Please join the waitlist here.