Loading...
Loading...
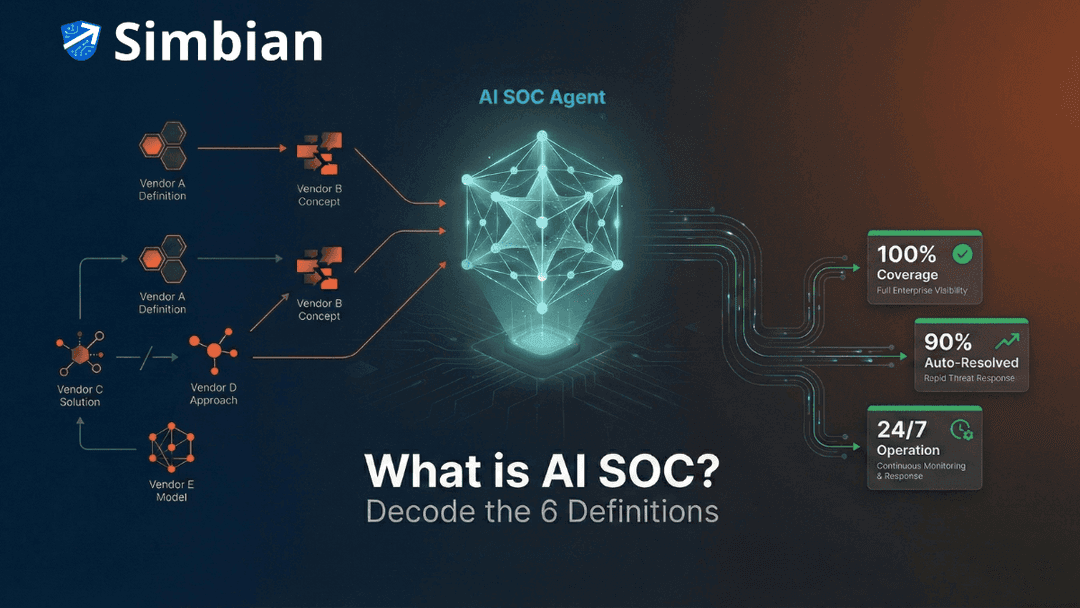
Ask five cybersecurity vendors "what is AI SOC?" and you'll get six different answers. One will tell you it's securing AI models themselves. Another promises an autonomous SOC that eliminates your entire analyst team. A third rebranded their decade-old SOAR platform with AI marketing. The fourth offers a co-pilot that assists your analysts. The fifth focuses on smarter detection rules. And the sixth—the one gaining traction on Gartner's 2025 Hype Cycle—talks about AI SOC agents that autonomously investigate and respond to threats.
The market confusion is understandable given the rapid technology evolution happening simultaneously across multiple fronts, across new vendors and legacy incumbents. It’s important, however, to understand the distinctions, as this determines whether your AI investment becomes the next evolution of SOC automation or another underutilized tool in an already sprawling security stack. Budget allocated to the wrong category won't solve your alert overload, reduce investigation time, or deliver the 90 percent auto-resolution rates that emerging AI SOC deployments are achieving.
Understanding what each category does and what it doesn't is essential to separating marketing positioning from technical capability.
SOC for AI (Completely Different Use Case): Some vendors use "AI SOC" to describe securing AI systems themselves—protecting language models, API endpoints, and generative AI applications from adversary attacks. While this is a key security concern, it has nothing to do with defending your enterprise applications and infrastructure. When a vendor talks about "securing your AI models," they're addressing a problem entirely different from alert triage and threat response. Skip this if your concern is AI for SOC.
AI-Only SOC (Vision, Not Reality): A few vendors describe their solution as an AI-only SOC that replaces your entire analyst team. The pitch is attractive: eliminate human error, operate 24/7 at machine speed, and remove the cost of human analysts entirely. But the reason organizations have analyst teams is because making security decisions requires understanding your business, your threat landscape, your asset criticality, and the context around what's normal in your environment. AI systems don't yet have the contextual reasoning required to operate entirely independently. “Will AI replace SOC Analysts?"
Next-Gen SOAR Automation (Old Tool, New Label): Some vendors are rebranding their SOAR platform with "AI" marketing and claim they're solving the problem of scaling automation. But SOAR fundamentally requires you to anticipate attacks and pre-write playbooks for known scenarios. Gartner deprecated SOAR in 2025 precisely because playbook-based automation cannot adapt to novel AI-driven attacks that deviate from predefined scripts. Putting an AI wrapper on SOAR doesn't change its core architectural limitation: it still escalates to humans the moment something deviates from the script.
Cybersecurity Copilots (Assistive, Not Autonomous): Copilots like Microsoft Security Copilot or similar tools function as AI assistants to your analysts. They accelerate analyst productivity by roughly 50 percent, reducing investigation time per alert from 30 minutes to 15 minutes. Copilots are fundamentally reactive and human gated. An analyst initiates a query; the copilot surfaces relevant data; the analyst interprets it and makes decisions. This assistive model doesn't scale when alert volume explodes 10x. You still need a proportional analyst headcount to handle the alerts.
AI-Powered Detection (Smarter Alerts, Not Investigation): Detection-focused AI improves alert quality at the source by applying machine learning to SIEM, EDR, and threat intelligence rules. Intelligent detection tunes alert sensitivity based on context and identifies behavioral anomalies that signature-based rules miss. This is valuable for detection engineering teams. But it doesn't address the investigation-and-response problem. You still have thousands of higher-quality alerts requiring analyst investigation. AI-powered detection improves the signal-to-noise ratio; it doesn't eliminate the investigation bottleneck.
AI SOC Agent (Autonomous Investigation and Response): AI SOC agent represents the category Gartner identified on its 2025 Hype Cycle as the emerging standard for scaling security operations. These are autonomous software systems that independently triage, investigate, correlate, and respond to alerts using real-time contextual reasoning. Unlike copilots that wait for analyst prompts, AI SOC agent autonomously uses business context with security signals to make investigation and response decisions without human involvement.
AI SOC agents operate at machine speed 24/7, investigate 100 percent of alerts (not just 60%), identify campaigns across thousands of daily alerts, and execute safe containment actions autonomously.
This is the only AI SOC category that fundamentally changes the scale of security operations, not just the speed of individual analysts.
AI SOC is already demonstrating its return on investment every day in enterprises and service providers around the world. For Simbian’s customers, the numbers say it all:
100% coverage of security alerts – everyone gets investigated
24/7 and off-hours coverage with no additional staff
90% auto-resolved alerts with evidence-based decisions
Reduced MTTR & MTTC
No more Playbook updating or tool migration
Results in less than a week
For 2026, make sure that your next security investment delivers the results you are looking for.
Book a demo with Simbian and begin your journey of getting to know AI SOC Agents.