Loading...
Loading...
On July 19, Microsoft sounded the alarm on a pair of SharePoint Server zero-days, CVE-2025-53770 and CVE-2025-53771, together called ToolShell or E-Colleague.
By the time the CVEs had a name, attackers had already operationalized them, scripting payloads for rapid, wide-scale exploitation campaigns.
Within 48 hours, over 100 organizations, including U.S. nuclear agencies, confirmed compromises. And as of this writing, nearly 9,000 internet-facing SharePoint servers remain exposed.
This isn’t your typical “patch-it-when-you-get-to-it” CVE. It’s a live-fire, multi-vector breach that requires more than a band-aid. It demands coordinated action.
With CISA issuing federal agencies a July 23 deadline, the clock isn’t just ticking—it’s strapping on a parachute.
Welcome to the part of cybersecurity where passive isn’t just dangerous. It’s an invitation.
Is this one of those “click and you’re screwed” bugs?
Worse. It’s “don’t even click and still get screwed.” Think EchoLeak but with less whimsy and more data exfiltration.
No user interaction. No file downloads. Just having an exposed SharePoint server is enough to land you in the blast radius.
What makes this more dangerous is that attackers are chaining these vulnerabilities with others—such as CVE-2025-49704 and CVE-2025-49706—to bypass security patches issued in May.
Once attackers get a foot in the door, even patched systems can remain compromised.
This campaign is powered by a modified strain of ToolShell, a remote access trojan tied to Chinese espionage groups. In this variant, ToolShell is embedded directly into SharePoint workflows, masquerading as legitimate traffic while burrowing deep into the network.
The ToolShell exploit works in 3 stages:
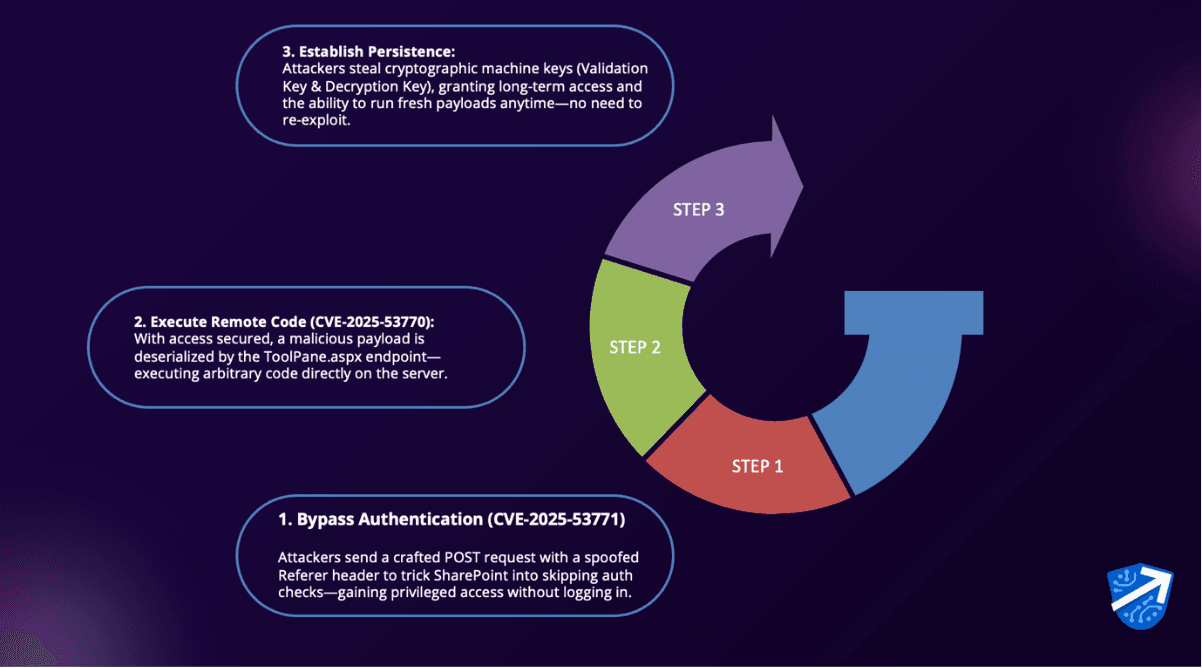
Vulnerable:
SharePoint Server 2016/2019/Subscription Edition (self-hosted)
End-of-life editions—2010/2013—may still be targets
Not affected: SharePoint Online (M365-hosted)
Exposure snapshot: Enterprises with self-hosted SharePoint, especially those directly internet-wired, face the highest risk profile.
If you’re managing an on-prem deployment of SharePoint and haven’t applied Microsoft’s July 2025 security update, assume exposure. If you’re unsure whether your SharePoint servers are accessible from the internet, unpatched, or logging strange traffic—you’re not just at risk, you’re already late.
This is a zero-day vulnerability that is being actively exploited by threat actors. Situations like this require an immediate multi-pronged response from security teams.
Prevention: First is to prevent abuse going forward. Microsoft’s blog outlines the steps you must take on your SharePoint servers to protect them going forward.
Threat Hunt: Second is to have your Threat Hunters check if your servers are already compromised. Microsoft’s blog shares KQL queries that Defender users can use.
Investigation: Third is to have your SOC analysts do additional diligence around specific alert types outlined in the blog.
Despite clear guidance on Microsoft’s blog, security teams are still left to figure out a lot.
Is your organization impacted by this vulnerability?
Does your organization use the impacted SharePoint versions? Are they patched already? Are they exposed to untrusted traffic?
Our organization does not use Defender. What do you do?
The hunt queries that Microsoft shared work only with Defender. What if your organization uses other detection tools? You must figure out the queries yourself. You must also figure out the alert types in your tools that potentially signal compromise.
You are compromised. What next?
Let’s say the hunt queries from Microsoft, or the equivalent in your tools, return results for you. Or let’s say you did get alerts of the type mentioned in the blog. You are compromised! Now starts the urgent all-hands exercise of figuring out how deep the threat actor went in your network. How much damage is already done.
As you can see, there is a lot of homework left for security teams to figure out, and it needs to happen ASAP. Every hour wasted in this is an hour more for the threat actor to spread in your network.
Our suite of AI Agents is intended to activate a fully coordinated response across every security function—automated, contextual, and incredibly fast.
Detect
The Threat Hunt Agent ingests threat intel (IOCs, TTPs, behavior patterns) and creates hunt queries tailored for your unique environment including Splunk, Chronicle, QRadar and dozens of detection tools and log stores for evidence of exploitation. So, your security team isn’t wasting time in the busywork of mapping queries to your tools.
Investigate and Respond
If your threat hunt or your existing detections indicate potential compromise, the SOC Agent automates investigation to filter out noise from signal, so your security team can be focused on true positives. It also automates remediation—quarantining infected assets, revoking tokens, and initiating playbook-driven containment. No more waiting for manual coordination.
Prevent
The purpose of Simbian’s VRM Agent is to understand which vulnerabilities are relevant, by correlating SBOMs, asset inventory, and exploit details to identify impacted systems—and push prioritized patching workflows. So, your team can go fast from vulnerability disclosure to patching.
This isn’t a patchwork of tools. It’s a system of AI Agents that speak the same language, work from the same intel, and act like a unified force. One detects, another remediates, a third communicates—without dropping the baton.
When vulnerabilities go from unknown to exploited in 24 hours, your only edge is speed. Simbian delivers that speed—not by adding more hands, but by deploying the right minds.
Simbian’s AI Agents aren’t standalone automation bots. Each agent (Threat Hunt, AI SOC, AppSec/VRM, GRC/CTEM) operates on a unified knowledge graph—Context Lake™, that fuses SIEM alerts, asset inventory, vulnerability findings, tribal knowledge, and ticket histories. This brings three decisive advantages:
Proactive, Not Reactive: AI Agents leverage enrichment from each other—SOC triage is better informed by ongoing AppSec exposure and Threat Hunt context, elevating detection quality and minimizing alert fatigue.
Speed of Response: Simbian Agents operate 24x7x365, shrinking detection and remediation windows by correlating signals across SIEMs, cloud, and endpoint telemetry in real time. There’s no hand-off or waiting on Tier-2 escalations.
Situational Awareness: Because every agent works from the same context lake, response automation is always risk-context-aware, preventing overreaction (false shutdowns) or blind spots (missed lateral movement).
Consistency and Auditability: Automated propagation of findings and response across functions ensures consistent risk posture and easier compliance tracking—a must for auditors and GRC programs.
Human Analyst Relief: AI agents handle repetitive triage, IOC translation, and asset scoping, freeing expert analysts for higher-order investigation and strategic defense engineering.
Both. Neither. Call it an existential crisis in the form of a blog.
Because this is bigger than SharePoint. It’s about how your security posture either leans on coordinated chaos—or coordinated agents. Incidents like these are where platformization shines. With agents working across AppSec, SOC, and Threat Hunt, you're not just buying tools—you’re buying time, speed, and intelligence.
But if you are curious how our agents can help keep SharePoint (and the rest of your stack) from leaking like a sieve—you know where to find us.