Loading...
Loading...

AI isn't just for chatbots anymore. These smart agents are getting really good at handling complex stuff, even in cybersecurity. But hooking them up to all the different security tools and data feeds? That's been a real headache – needing a unique adapter for every single connection. This is where the Model Context Protocol (MCP) steps in. Think of it like the USB-C of the AI world, an open standard pushed by Anthropic to make connecting things way easier. The idea is simple: give AI, especially the big language models (LLMs) and agents, one standard way to talk to tools, data, and systems.
For cybersecurity folks, this is a big deal. It can allow AI to smoothly chat with your security products, grabbing real-time threat info, enforcing rules, and even kicking off automated responses like never before. Let's break down what MCP is, how it's showing up in security tools, and where it's headed.
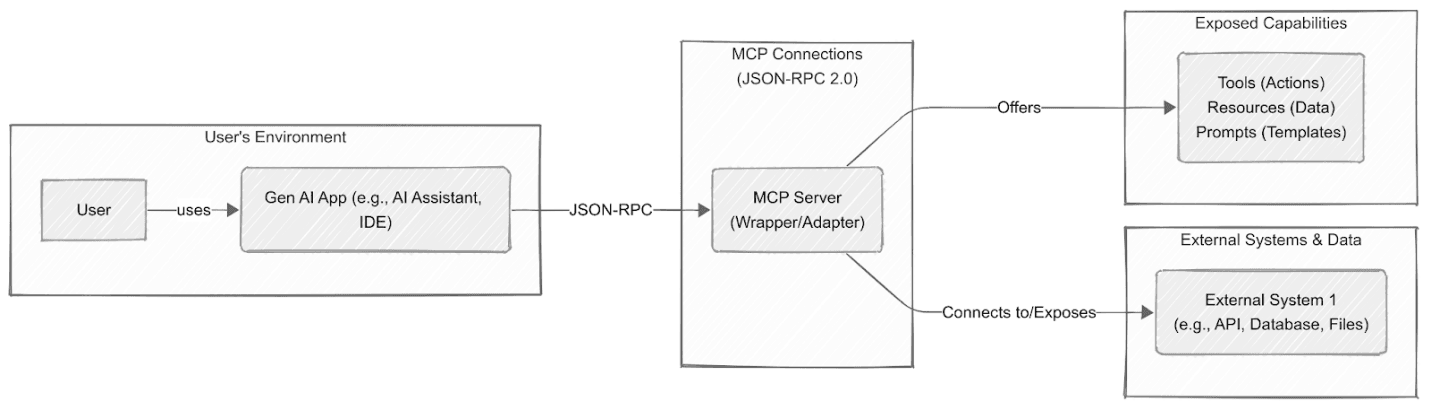
MCP uses a pretty standard client-server setup, but it's built with AI in mind. Here are the main players:
MCP Host (aka. Gen AI App): This is the app you're actually using – maybe an AI helper like Claude Desktop, a code editor like Cursor, or an AI SOC tool such as Simbian. It manages the connections to different MCP Servers and usually talks to the LLM, making sure you're okay with any actions the AI wants to take.
MCP Client: Lives inside the Host. Each client keeps a dedicated connection to one MCP Server using a format called JSON-RPC 2.0. It handles the protocol details, figures out what the server can do, and manages the back-and-forth messages.
MCP Server: This acts like a translator or wrapper. It takes the features of an outside system (like a security tool's API, a database, or even local files) and makes them available in the MCP format. These servers can be pretty simple and built using different programming languages such as Go or Python.
MCP has a few basic message types, called "primitives." The important ones for security are:
Tools (Model-controlled): These are like buttons the AI can press to do things in the connected system (think isolate_this_computer, check_threat_database, block_this_IP). This is how MCP lets AI take action, which makes security around these tools and getting your permission super important.
Resources (Application-controlled): This is data given to the AI to help it understand the situation (like security policies, system logs, vulnerability lists, threat updates). It makes the AI smarter without letting it change things.
Prompts (User-controlled): These are like pre-written instructions telling the AI the best way to use certain tools or data for tricky tasks.
This split between getting data (Resources) and taking action (Tools) is smart for security. It means you can set up different rules for each, following ideas like giving the AI only the permissions it absolutely needs (least privilege). MCP also lets things discover capabilities on the fly and talk back and forth. There's even a feature called "Sampling" where the server can ask the client to run an AI task. This allows for complex AI chains but needs careful control by the client/host, or it could be misused.
MCP's standard approach could really boost different security jobs by letting AI agents use specialized tools through one common language:
Endpoint Detection & Response (EDR): Imagine AI agents using MCP to ask your EDR (like SentinelOne, CrowdStrike, Microsoft Defender, Tanium) how an endpoint is doing, grab logs, start a scan, or lock down a machine. There's already an MCP server for Velociraptor, and others are definitely in the works. Security Information & Event Management (SIEM): Agents could use MCP to query your SIEM (like Splunk, Microsoft Sentinel, QRadar, Chronicle SecOps) for logs, connect the dots between events, summarize incidents, or kick off automated response plans (SOAR). The AI can look at SIEM alerts (Resources) or run specific searches (Tools).
Access Control / Privileged Access Management (PAM): This is a big one. AI agents could check access logs, look at permissions, or enforce rules by connecting MCP to your PAM/IAM systems. We're seeing things like the Netwrix Access Analyzer MCP server for asking questions in plain English and platforms like SGNL and QueryPie offering MCP-specific controls. But letting AI change access rules (Tools)? That needs serious thought and solid approval steps.
Threat Intelligence: Agents can ask platforms like MISP or OpenCTI for info on Indicators of Compromise (IOCs) using specific MCP servers.
Security Orchestration, Automation, and Response (SOAR): MCP could become the AI's control panel for SOAR, letting agents pick and run automated playbooks and tools based on what's happening in an incident.
Other Tools: The list is constantly growing! Servers are popping up for firewalls (Palo Alto Networks), vulnerability scanners (Snyk, Trivy), cloud security (Orca Security), and more.
Basically, MCP acts like a standard remote control for AI agents in the SOC. It doesn't replace your security tools; it just gives AI a common way to use them. But how well this works – and how secure it is – really depends on the quality and security of the MCP servers connecting to these crucial tools. A weak MCP server wrapping your EDR or firewall could be a major risk.
The MCP world is growing fast. More servers, more developer kits (SDKs) in different languages, and big AI and cybersecurity companies are getting on board. Here's what we might see:
Smarter, More Independent Agents: As LLMs get better, agents will handle more complex security tasks on their own, with less direct human input.
Specialized Security Tools for MCP: Expect more tools like MCP PAM and AI Security Posture Management (AI-SPM) built just to manage AI agents using MCP.
Getting More Formal: We might see things like certified servers, standard ways of logging, and trusted places ("App Stores") to get servers, making things more secure and reliable.
The Standard for AI in Security Tools: MCP could become the go-to way for AI to talk to security tools, letting us use plain English to ask questions and give commands.
Because MCP is open-source, it grows quickly, but that also means the community needs good security habits and strong external checks MCP mixing with AI SOC points to a future SOC where AI agents do a lot of the grunt work (analysis, response), letting human analysts focus on oversight, tricky problems, and strategic threat hunting.
But – and it's a big but – as with any new protocol, this potential comes with real security risks. Bad servers, stolen credentials, prompt injection tricks, and weak access controls are serious threats we can't just ignore. MCP will only be truly useful in cyber defense if we tackle these problems head-on. That means carefully checking servers, always getting user permission for actions, using strong authentication and input checks, watching everything closely, and using emerging security ideas like MCP PAM that are built for this AI agent era.